Simplifying IT
for a complex world.
Platform partnerships
- AWS
- Google Cloud
- Microsoft
- Salesforce
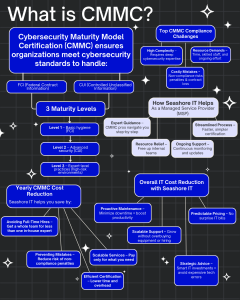
As cybersecurity threats escalate, particularly within the federal supply chain, the Cybersecurity Maturity Model Certification (CMMC) has become a crucial requirement for organizations working with the U.S. Department of Defense (DoD) and other federal agencies. CMMC ensures that businesses handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) meet specific cybersecurity standards to safeguard national interests.
This infographic by Seashore IT breaks down what CMMC is, its maturity levels, top compliance challenges, and how a Managed Service Provider (MSP) can reduce the cost and complexity of achieving certification.
CMMC is structured across three progressive levels, each representing increasing cybersecurity capabilities:
Level 1: Basic Cyber Hygiene – Focused on protecting FCI with foundational security practices.
Level 2: Advanced Security – Required for handling CUI, this level demands intermediate safeguards aligned with NIST 800-171.
Level 3: Expert-Level Practices – Designed for organizations in high-risk environments, requiring robust, proactive threat protection and continuous monitoring.
Whether you’re bidding on a DoD contract or working in a critical infrastructure supply chain, identifying your required level is the first step toward compliance.
Achieving and maintaining CMMC compliance is not a one-time task—it’s an ongoing journey that poses several challenges:
High Complexity: Requires deep cybersecurity knowledge and adherence to technical standards.
Resource Demands: Significant time, staff, and continual effort are needed to implement and sustain controls.
Costly Mistakes: Non-compliance can result in contract loss, penalties, or disqualification from bids.
For many SMBs, these challenges are difficult to manage alone, which is where managed CMMC services come in.
Seashore IT offers tailored support to help organizations navigate and sustain CMMC compliance. Their end-to-end support includes:
✅ Expert Guidance: CMMC-certified professionals walk you through compliance requirements step-by-step.
✅ Streamlined Certification Process: Faster, simpler onboarding with fewer administrative roadblocks.
✅ Ongoing Monitoring: Continuous security updates and compliance maintenance.
✅ Resource Relief: Free up internal IT teams to focus on core business operations.
This approach is ideal for contractors who need affordable CMMC support without hiring a full-time specialist.
One of the biggest concerns surrounding CMMC is cost—but Seashore IT delivers major savings through:
💸 Avoiding Full-Time Hires – Access a full support team for less than one in-house expert.
🔁 Proactive Maintenance – Minimize downtime, improve security, and boost productivity.
🔒 Mistake Prevention – Reduce the risk of audit failures and non-compliance penalties.
📊 Predictable Pricing – Transparent pricing model with no surprise IT bills.
⚙️ Scalable Services – Pay only for the support you need, and scale as you grow.
Additionally, they help clients achieve efficient certification, reducing time, stress, and overhead associated with audits and documentation.
CMMC is no longer optional for government contractors—it’s a strategic necessity. But compliance doesn’t have to be a burden. With the right partner, businesses can achieve certification faster, avoid costly mistakes, and reduce IT expenses across the board.
Seashore IT is a trusted Managed Service Provider that helps organizations meet CMMC standards while simplifying the process and keeping costs low. If you’re navigating compliance or preparing for an upcoming bid, their support can be the edge you need to win contracts and protect sensitive data with confidence.